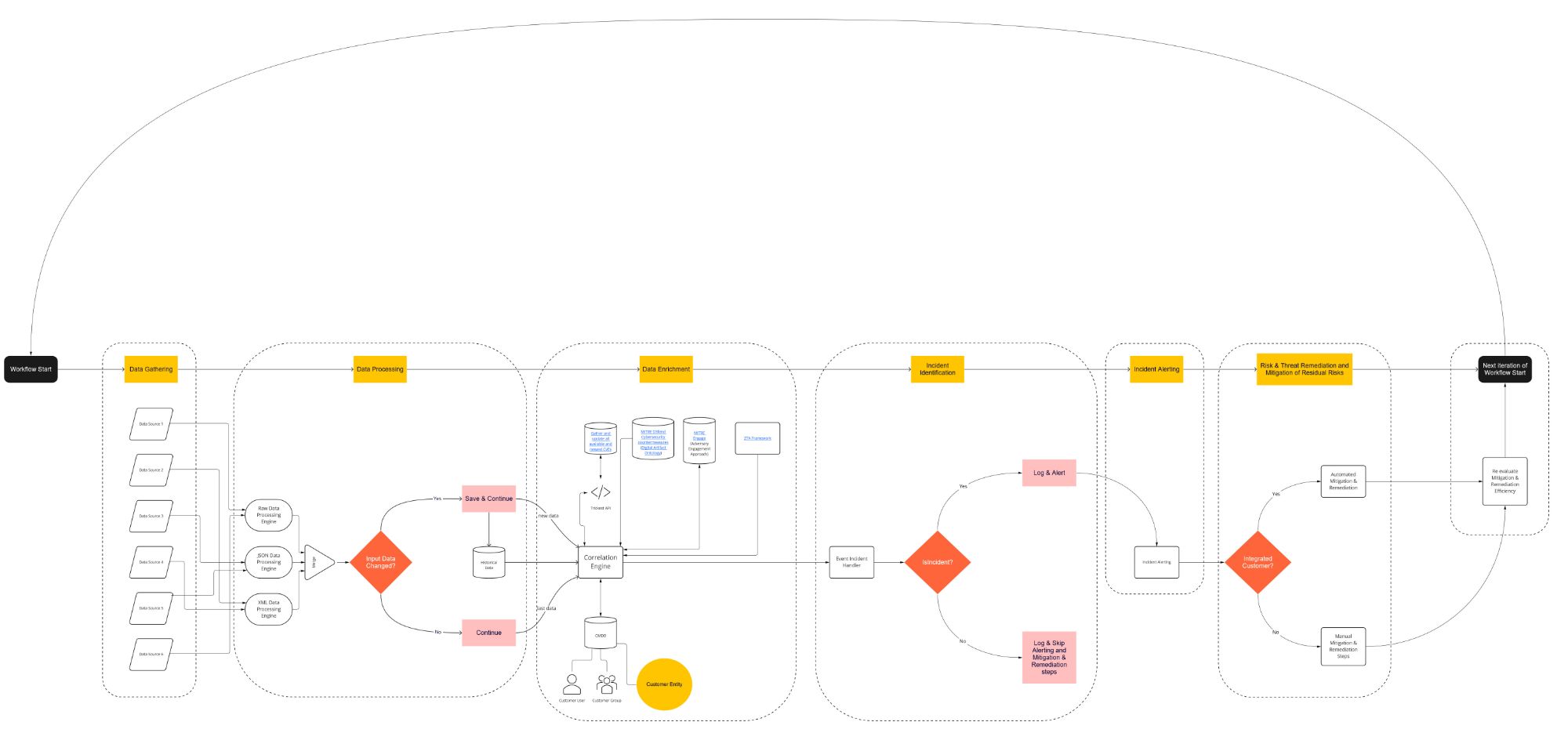
Data Gathering
Collecting information across different connected resources - websites, forums, APIs, IMs, networks, applications, IoT
Data Processing
Normalizing ingress data over raw, JSON and XML Data Processing Engines (DPE)
Data Enrichment
Correlating DPE data with data sources for automated Risk Assessment & Vulnerability Exploitability - integrated CMDB, Trickest API, MITRE D3fend, MITRE Engage, ZTA
Security Baseline Breach Identification
Event Problem Handler evaluates if defined Security Baseline has been breached to trigger the subsequent actions
Security Baseline Breach Alerting
Alerting on identified Incident with information about Risk & Threat Remediation and Mitigation steps to be executed
Risk & Threat Remediation and Mitigation of Residual Risks
Automated remediation and mitigation based on known strategies or Manual Mitigation & Remediation Steps to be executed
Reexecution of the workflow
AI/ML engine driven validation and continuous development of effectivity of automated risk and threat mitigation strategies